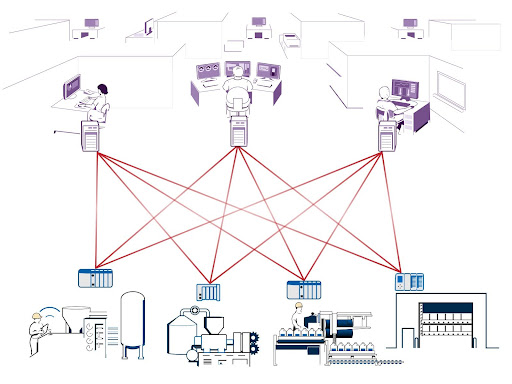
Beyond data transactions, understanding the relationship between clients and servers plays a significant role in cybersecurity.
What makes a device fill the role of a server or client? And, more importantly, how can you use that information to strengthen your network security and mitigate insecurities?
The best place to start with this topic is to loosely define what makes software act as a server or as a client. But throughout this blog, keep in mind that the two are not mutually exclusive—some devices can be both a server and a client. When playing the role of a server the key trait is that the server device is always listening.